6.2 Configuring SSO with Okta (SAML)
If your organisation uses Okta as an IdP, you can use Okta for configuring SSO for accessing various Thredd services, for example, Thredd Portal. This page describes the steps for using the 2.0 version of Security Assertion Markup Language (SAML) protocol for setting up SSO.
As a client, you would already have an account on the Okta Administration Console.
Setting up SSO is not mandatory, but is recommended.
6.2.1 Summary of Steps
The steps involve:
- Creating a SAML app for your SSO connection to Thredd services.
- Adding configurations from Thredd including the SSO URLs and the Entity ID.
- Mapping fields associated with the users defined by Okta with those used by your app.
- Sharing the Metadata URL with Thredd.
6.2.2 Configure SSO
- Log in to the Okta Administration console.
- From the left-hand menu, select Applications.
- Click on Create Application.
- Select SAML 2.0 and click Next. The next page appears.
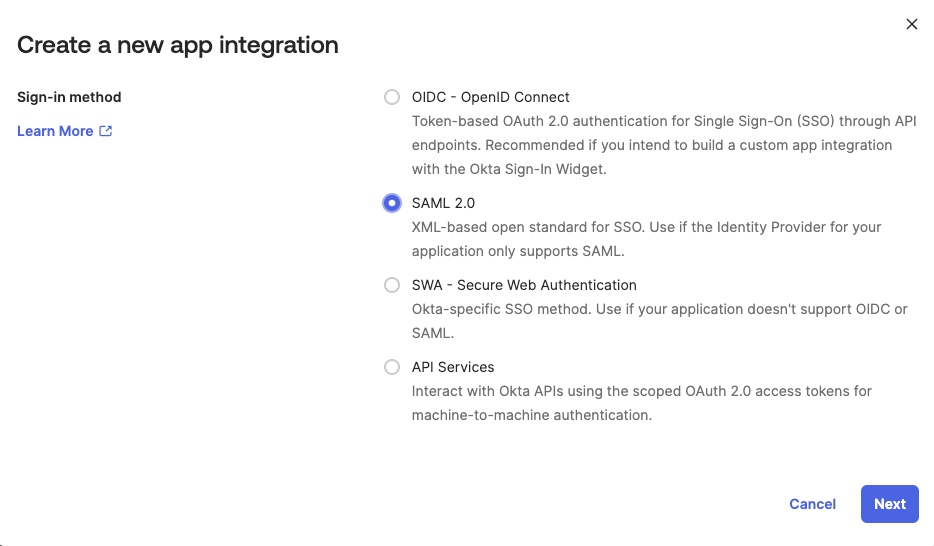
- Enter a name for the app that accesses Thredd services in App name and click Next. The next page appears.
- Add the provided URLs in Single Sign-on URL (ACS URL) and Audience URL (entity ID).
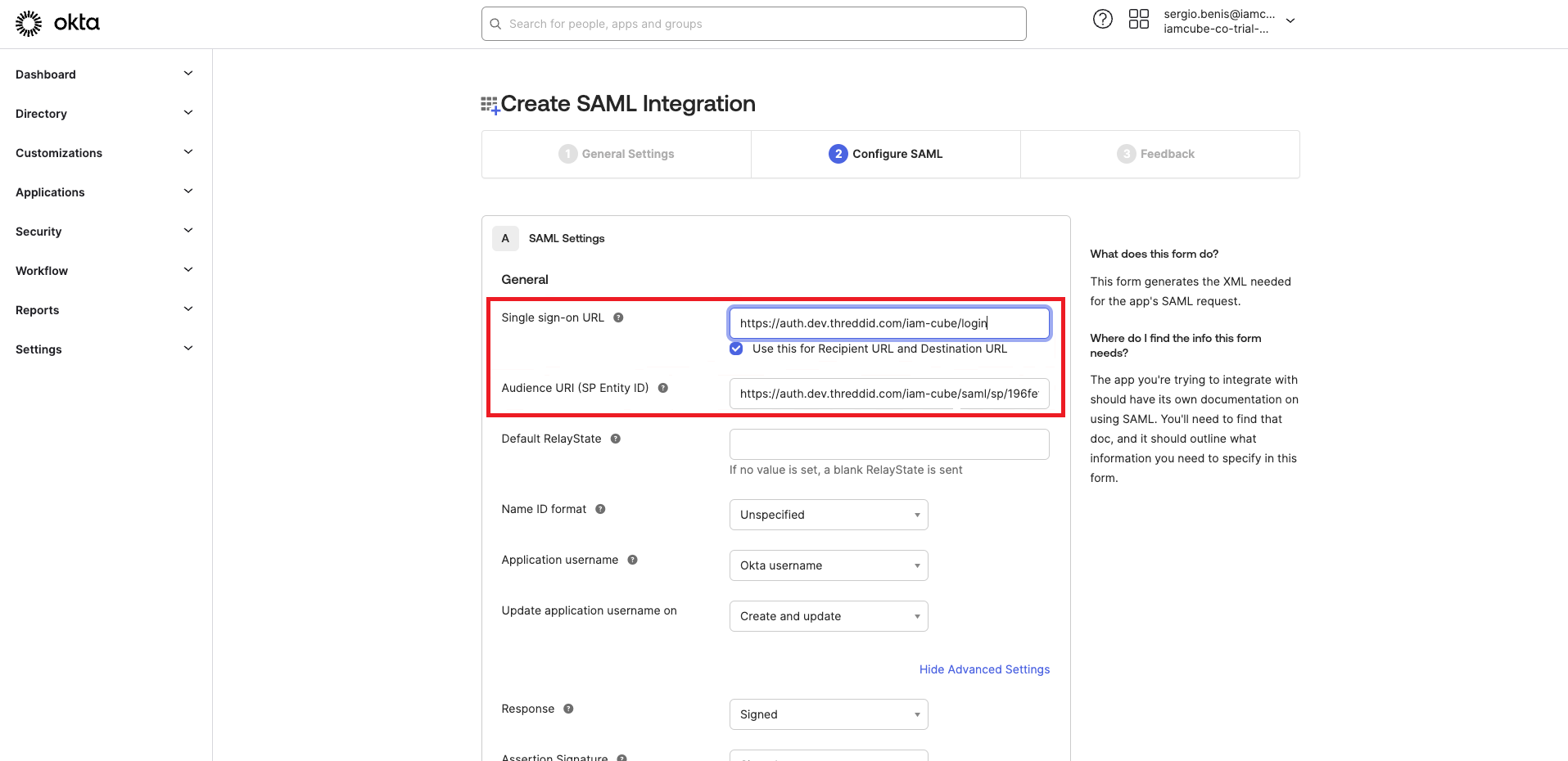
-
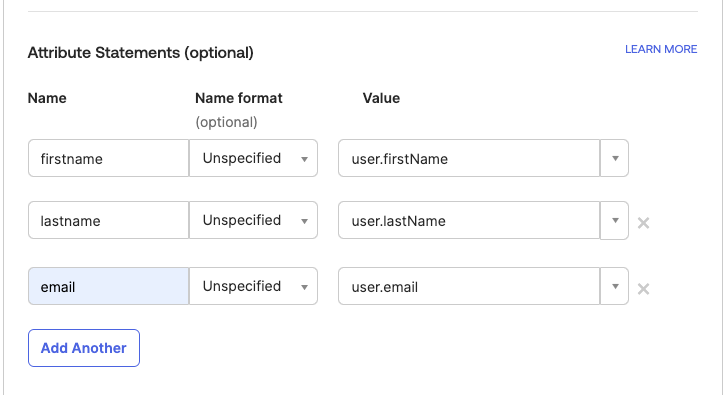
Scroll down on the same page and configure the following Attribute Statements:
- Enter an attribute name in the Name column.
- Select a value in the Value column.
- To add another entry, click the Add Another button.
- Repeat steps a and b.
- Click Next.
- In the displayed page, select This is an internal app that we created and click Finish.
- In the displayed Metadata Data details that appear, share the Metadata URL with Thredd.
You can then assign the application to the users or groups who will be using the Thredd services.